Many sites use third-party CDN (Content Delivery Network) services that store static content on multiple geographically distributed servers. When a user requests content, the request is processed by the CDN server closest to the user. This approach is particularly actively used on sites that operate with large traffic volume, e.g. sites providing multimedia content. The use of CDN speeds up the site for the user and also reduces the load on the server, where the content is hosted.
A common practice is to host all of a site's static content on a separate domain, which will be served using CDN, while the site's main domain will run without it.
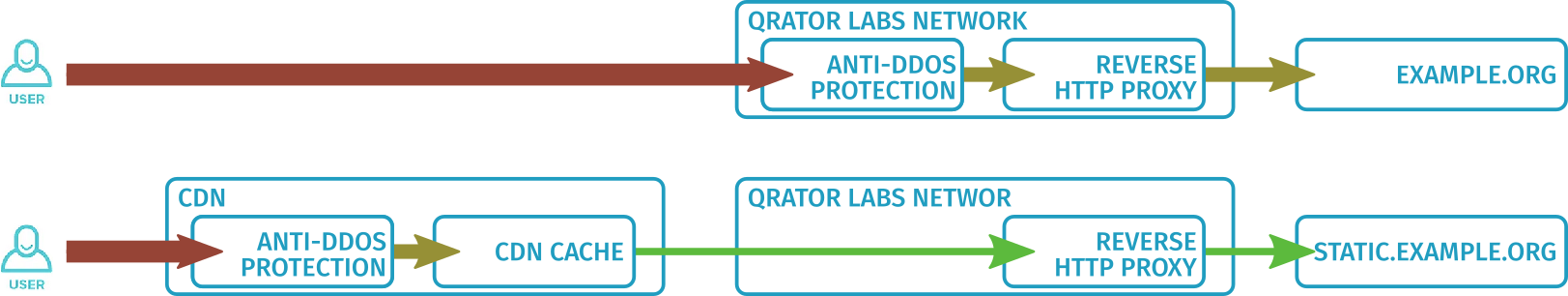
If the server where the content is hosted is under Qrator Labs protection (i.e. is an upstream), then additional security settings are required to allow traffic from the CDN network. The CDN is not just outside the customer's network, but also outside the Qrator Labs network. Therefore, requests from CDN to this upstream go the same way as requests from an abstract user. However, their number and nature can be noticeably different. If configured incorrectly, such requests can trigger DDoS attack false positives in the Qrator Labs network. This will immediately affect all users who receive content through CDN.
Qrator Labs offers its own service Qrator.CDN, as well as integrations with many popular CDN service providers. Regardless of the specific provider, the general principle is to correctly identify requests from CDNs and always consider them as legitimate.
The specific way to determine requests depends on which provider's CDN you're using. G2O request signature authentication is used for some providers, while for others, a whitelist-based IP address checking is used. There are also different ways to configure other CDN settings: the settings for Qrator.CDN are available directly in a special dashboard section or are configured by the Qrator Labs technical support team, while for most providers you have to configure them at the provider's site, separately from Qrator Labs.
Working with Ngenix, Akamai and G-Core
For customers using CDNs from Ngenix, Akamai or G-Core, Qrator Labs automatically adds the IP addresses of the respective networks to attack protection exceptions. So, all traffic passed by CDN is guaranteed to reach the upstream.
All settings are made on the website of the corresponding CDN. Qrator IP should be specified as the upstream for CDN.
Working via G2O
Many CDN providers support request authentication protocol G2O. Under this protocol, two HTTP headers are added to each request. One contains certain additional data about the request, including a randomly generated request ID. The second header contains a signature based on that data. The signature uses a key, one part of which is known to the Qrator Labs network and is used for verification. This way the Qrator Labs network can verify that the request was sent from the CDN.
All the settings are done on the website of the respective CDN. Qrator IP should be specified as the CDN upstream.