Sending web server logs to Qrator Labs servers allows you to analyze and clean up HTTP traffic going to these web servers at the application layer (L7 under the OSI/ISO model) in situations where it is not technically possible to analyze HTTP traffic itself.
For instance, it is recommended to configure log sending if you're using reverse TCP proxy Qrator Labs. This proxy analyzes traffic at the transport layer (L4), but, with the help of log analysis, can also protect against some application layer (L7) attacks.
To transmit logs to the Qrator Labs network:
- Choose the IP addresses and ports for log sending
- Configure the log format.
- Configure log collection and sending.
Warning
For analysis, you need the logs of the web server on your network that receives external requests first, regardless of where it routes or proxies them later. In this case, only access logs are needed. It is not necessary to send error logs.
1. Choose the IP addresses and ports for log sending
This step should be done by you and Qrator Labs technical support team. On your side, you need to set which IP address the logs will be sent from. On the Qrator Labs side, the IP address and port of the log listener will be assigned. The assigned IP address may be different from Qrator IP specified in your dashboard.
2. Configure the log format
Configure the server such that access logs are written in a certain format from which the Qrator Labs reverse TCP proxy can extract all the information needed for analysis. Log format requirements may change in the future, in which case Qrator Labs tech support specialists will inform you about the changes beforehand.
Below are the current log formats for popular web servers.
Specify the following line in the log_format option.
'2xFFFFFF|:,_|$bytes_sent|:,_|$http_accept|:,_|$http_accept_encoding|:,_|$http_accep
t_language|:,_|$http_cookie|:,_|$http_host|:,_|$http_referer|:,_|$http_user_agent|:,
_|$http_x_forwarded_for|:,_|$remote_addr|:,_|$request|:,_|$request_time|:,_|$status|
:,_|$time_local|:,_|$upstream_response_time|:,_|$http_x_requested_with|:,_|$http_aut
horization|:,_|$remote_port|:,_|-|:,_|$msec|:,_|'
Specify the following line in CustomLog.
'5xFFFFFF|:,_|%O|:,_|%{Accept}i|:,_|%{Accept-Encoding}i|:,_|%{Accept-
Language}i|:,_|%{Cookie}i|:,_|%{Host}i|:,_|%{Referer}i|:,_|%{User-Agent}i|:,_|%{X-
Forwarded-For}i|:,_|%a|:,_|%r|:,_|%{ms}T|:,_|%s|:,_|%t|:,_|%D|:,_|%{X-Requested-
With}i|:,_|%{Authorization}i|:,_|%{remote}p|:,_|%{sec}t.%{msec_frac}t|:,_|-|:,_|'
Specify the following line when configuring request logging according to the Configuring Request Logging guide.
'3xFFFFFF|:,_|$RESPONSE_SIZE|:,_|$Accept|:,_|${Accept-Encoding}|:,_|${Accept-
Language}|:,_|$Cookie|:,_|$Host|:,_|$Referer|:,_|${User-Agent}|:,_|${X-Forwarded-
For}|:,_|$CLIENT_IP|:,_|$CLIENT_PORT|:,_|$HTTP_REQUEST|:,_|$RESPONSE_MSECS|:,_|$HTTP
_STATCODE|:,_|$DATE_YYYY/$DATE_MM/${DATE_DD}_$TIME_HH24:$TIME_MM:$TIME_SS|:,_|$HTTP_
KEEPALIVE|:,_|$SERVER_IP|:,_|$SERVER_PORT|:,_|$BIGIP_CACHED|:,_|${X-Requested-
With}|:,_|${Authorization}|:,_|$CLIENT_PORT|:,_|$TIME_MSECS|:,_|-|:,_|'
Insert the following snippet into configuration file HAProxy.
capture request header Accept len 4096
capture request header Accept-Encoding len 4096
capture request header Accept-Language len 4096
capture request header Cookie len 16384
capture request header Host len 4096
capture request header Referer len 4096
capture request header User-Agent len 4096
capture request header X-Forwarded-For len 4096
capture request header X-Requested-With len 4096
capture request header Authorization len 4096
log-format "4xFFFFFF|:,_|%B|:,_|%[capture.req.hdr(0)]|:,_|%
[capture.req.hdr(1)]|:,_|%[capture.req.hdr(2)]|:,_|%[capture.req.hdr(3)]|:,_|%
[capture.req.hdr(4)]|:,_|%[capture.req.hdr(5)]|:,_|%[capture.req.hdr(6)]|:,_|%
[capture.req.hdr(7)]|:,_|%ci|:,_|%r|:,_|%Ta|:,_|%ST|:,_|%Tl|:,_|%Tr|:,_|%
[capture.req.hdr(8)]|:,_|%[capture.req.hdr(9)]|:,_|%cp|:,_|%Ts.%ms|:,_|-|:,_|"
3. Configure log collection and sending
Depending on the web server you use, you may have different ways of sending logs to Qrator Labs. The easiest way is to send logs directly from the web server if it supports such. A more universal solution is to use a log management system for any web server.
Note that the log listener on the Qrator Labs side accepts logs via syslog over the TCP transport protocol. Some web servers only support syslog over UDP or over Unix sockets. In that case, it is recommended to collect them using a logging system that would redirect the logs to Qrator Labs.
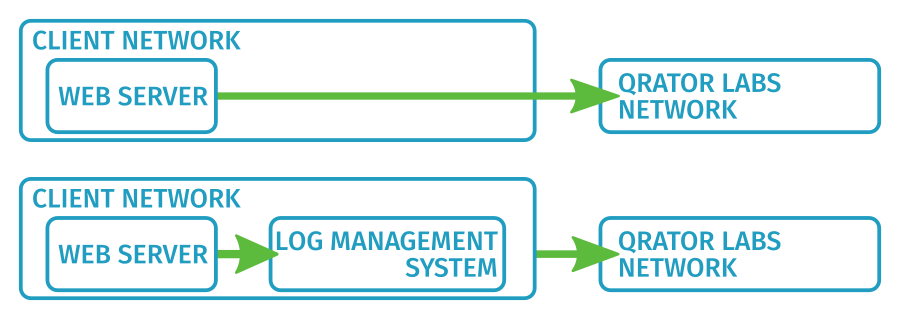
Send logs directly
If the web server handling user requests is capable of sending logs to Qrator Labs via the syslog protocol itself, then you only need to configure that web server accordingly. For example, instructions on how to send logs directly from F5 BIG-IP can be found here: Configuring BIG-IP to log to a remote syslog server.
To use the secure TLS to send logs, even if the web server itself does not support this protocol, you can use the optional Stunnel as described here: SSL Encrypting Syslog with Stunnel.
Using log management systems
A logging system is software that can act as an intermediate host between your web server and Qrator Labs log receiver. Examples of such systems for Unix-like operating systems are rsyslog and syslog-ng; for Windows – Snare. When selecting a logging system, note that Qrator Labs accepts syslog over TCP transport protocol, not UDP.
Note
Popular logging systems also support encryption of sent logs using TLS, for example:
Interaction between the web server and the logging system can be configured in a variety of ways, including reading logs from a text file, over a Unix socket, or over TCP or UDP. The method you choose depends on whether the web server and the logging system are on the same server or on different servers.
You also usually need to configure the web server itself in order to send logs to the right file, socket, or address. Read more in the documentation for the particular web server you are using, e.g:
Warning
When using logging system rsyslog, you must additionally configure the action queues and their discard rules. You can read more here: Action Queue cfg discarding local messages.
rsyslog configuration examples
Below are examples of rsyslog configuration files for HAProxy and NGINX. The required configuration file should be placed in the /etc/rsyslog.d/ directory and then rsyslog should be restarted. To use TLS, it is also required to substitute the path to Qrator Labs certificate in the configuration file.
$AddUnixListenSocket /var/lib/haproxy/dev/log
if ($programname startswith 'haproxy') then {
if ($msg contains '4xFFFFFF') then {
$template codename-fwd,"<%PRI%>1 %timegenerated:::date-rfc3339% codename %syslogtag:1:32% - - %msg:::drop-last-lf%\n"
action(type="omfwd"
Target="<receiver IP address>"
Port="<receiver port>"
protocol="tcp"
queue.filename="codename-fwd-q1"
queue.discardSeverity="4"
queue.discardMark="25000"
queue.size="30000"
queue.highWatermark="10000"
queue.lowWatermark="0"
queue.timeoutEnqueue="500"
queue.maxDiskSpace="20m"
queue.timeoutWorkerthreadShutdown="-1"
queue.saveOnShutdown="on"
queue.type="LinkedList"
Action.ResumeRetryCount="-1"
template="codename-fwd"
)
}
}
$AddUnixListenSocket /var/lib/haproxy/dev/log
global(
DefaultNetstreamDriverCAFile="<path to the receiver certificate file>"
)
if ($programname startswith 'haproxy') then {
if ($msg contains '4xFFFFFF') then {
$template codename-fwd,"<%PRI%>1 %timegenerated:::date-rfc3339% codename %syslogtag:1:32% - - %msg:::drop-last-lf%\n"
action(type="omfwd"
Target="<receiver IP address>"
Port="<receiver port>"
protocol="tcp"
queue.filename="codename-fwd-q1"
queue.discardSeverity="4"
queue.discardMark="25000"
queue.size="30000"
queue.highWatermark="10000"
queue.lowWatermark="0"
queue.timeoutEnqueue="500"
queue.maxDiskSpace="20m"
queue.timeoutWorkerthreadShutdown="-1"
queue.saveOnShutdown="on"
queue.type="LinkedList"
Action.ResumeRetryCount="-1"
template="codename-fwd"
)
}
}
input(type="imuxsock"
Socket="/var/log/nginx/nginx.sock")
template(name="codename-fwd" type="string"
string="<%PRI%>1 %timegenerated:::date-rfc3339% codename %syslogtag:1:32% - - %msg:::drop-last-lf%\n"
)
if ($programname startswith 'nginx') then {
if ($msg contains '2xFFFFFF') then {
action(type="omfwd"
Target="<receiver IP address>"
Port="<receiver port>"
protocol="tcp"
StreamDriver="gtls"
StreamDriverMode="1"
StreamDriverAuthMode="anon"
queue.filename="codename-fwd-q1"
queue.discardSeverity="4"
queue.discardMark="30000"
queue.size="30000"
queue.highWatermark="10000"
queue.lowWatermark="0"
queue.timeoutEnqueue="500"
queue.maxDiskSpace="20m"
queue.timeoutWorkerthreadShutdown="-1"
queue.saveOnShutdown="on"
queue.type="LinkedList"
Action.ResumeRetryCount="-1"
template="codename-fwd"
)
& stop
}
}
input(type="imuxsock"
Socket="/var/log/nginx/nginx.sock")
template(name="codename-fwd" type="string"
string="<%PRI%>1 %timegenerated:::date-rfc3339% codename %syslogtag:1:32% - - %msg:::drop-last-lf%\n"
)
global(
DefaultNetstreamDriverCAFile="<path to the receiver certificate file>"
)
if ($programname startswith 'nginx') then {
if ($msg contains '2xFFFFFF') then {
action(type="omfwd"
Target="<receiver IP address>"
Port="<receiver port>"
protocol="tcp"
StreamDriver="gtls"
StreamDriverMode="1"
StreamDriverAuthMode="anon"
queue.filename="codename-fwd-q1"
queue.discardSeverity="4"
queue.discardMark="30000"
queue.size="30000"
queue.highWatermark="10000"
queue.lowWatermark="0"
queue.timeoutEnqueue="500"
queue.maxDiskSpace="20m"
queue.timeoutWorkerthreadShutdown="-1"
queue.saveOnShutdown="on"
queue.type="LinkedList"
Action.ResumeRetryCount="-1"
template="codename-fwd"
)
& stop
}
}
Qrator Labs certificates
To send data over the TLS transport protocol, you must use a Qrator Labs log receiver certificate.
Different receivers on the Qrator Labs side use different certificates. Contact Qrator Labs tech support to find out which receiver you need to send the logs to. You can also check the authenticity of the CA (certificate authority) that signed these certificates.
Save the required certificate to a file, e.g. /etc/rsyslog.d/codename-syslog-ca.crt, and specify this in the logging system configuration path. Configuration files for rsyslog can be found at rsyslog configuration examples.
-----BEGIN CERTIFICATE-----
MIIFoDCCA4igAwIBAgIUXrO0RMKji9GzhxuRKzgv1ctB4iYwDQYJKoZIhvcNAQEL
BQAwUTEZMBcGA1UEAwwQUXJhdG9yIFN5c2xvZyBDQTEUMBIGA1UECgwLUXJhdG9y
IExhYnMxHjAcBgkqhkiG9w0BCQEWD21haWxAcXJhdG9yLm5ldDAeFw0yMTA3MTIx
NTU4NDNaFw0yNjA3MTExNTU4NDNaME8xFDASBgNVBAoMC1FyYXRvciBMYWJzMRcw
FQYDVQQDDA4xNzguMjQ4LjIzOS4yOTEeMBwGCSqGSIb3DQEJARYPbWFpbEBxcmF0
b3IubmV0MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAusYLrODkJPkf
OhZzaLupR+yO1L5SxDka8tW89Mf8mYkpmLPVd42B/8Zw4aqR+YYmsvob8sJYlhv6
zPl1dRocPZ3qXkbvVRj+IrWWzKRvVIiN7RS/Ducw+PcDxWA+3Gq7YFO2z8nxctn2
YqfIUCsitjQAFxx/UNpCvk3w1gQUSsDh2rPvZZNy1DlmpKyOArkA8r3qaLqY55vk
qq37cHDsf+ycZxQ4cj8Yxj+yltX7XIx7nOcE/s2esb/fzeqB0fVxugZe3Cqumkq+
oI3m0NJsT/F35hu4eFlqK/yRvmwsFqgFBozZ2FuyxStWocYdKyYYIe3OX1NQSS2y
1f1FRPwae6MAydnotHmBRCWdrFK38y7AdmztcFN68qF9iKG5WhOk3sAg39Korlt/
86Ki3Eeggml4IkKPxi7bOW+fCVIJCN7y2eMMUlZVDabJk1Bq0nwZ1f+UEmYXBJ7L
Ys5rr71hpTcjYe2QFjZH6FtIRbMwlW5tLY31OR1iy9ybDZmirbQVfEXSdokDBZjm
W5UhrnWipO0XFek74WffnbGaOmbDUL4iFvfzR1qOO/YTB5LK3RzXZesl0kSk3InK
eXhcSTjeGLisxiSsGRlZqcJhA4tHywr0poIZvMeZHoejsTgvvAxhaCSX0NbWj88u
Qbrkl4FqzLJdtaAt3KhCtPfwaZi9QDMCAwEAAaNyMHAwHQYDVR0OBBYEFPWE0qob
GzPsWrrg22lwhjsAtqiHMB8GA1UdIwQYMBaAFGyR/xVNsHdETvLwhPDkBYlAEBAo
MAkGA1UdEwQCMAAwDgYDVR0PAQH/BAQDAgXgMBMGA1UdJQQMMAoGCCsGAQUFBwMB
MA0GCSqGSIb3DQEBCwUAA4ICAQANvNMmFbp9OEYGOFPnVAtCw5xaaOqJsAyB5iiv
fmIQyAyND4z02m5kUJ+bsSEBBH+6eHlwNgP/mm9zxdWFL6R4l6sYr1ePQVU5Dv6H
K1wbtv1ToNnH5cZjTIBOFaCfSnqjbl9hpzxdJFer0DNMqhsGUPi8GziKnyxMh+km
u2Ln/yYZHoAFM+fq9/5iR7m/WEcid6NJGg2/lWM2hAAiKIwO1JSCmUgjoZ+sLJpH
vYN7egBpDNJe2e9yzGrPT58IeCvs9yVUxd2XAuB+A+wVvs9ZEH9HCXzGUTfNK/O9
aSJoq8GeUfFLRFxdyx7i0il8htn4LkE0SIVdjdH5JkOLc3EdePVRuxNh/cCm2pYZ
QBjNybSTzC7Be6UXALIM2eHXPyYZcmnLoaqf+mkYoKWGPXZ2/PKNGjg4++6C6YS4
/Ah1G/SNKNv+5D6/9ybM0XHzBhAWhmgd7gU9gbOBhNoIAeTywubcim4qE0yRvtzB
EqECIjIyGcIQEqRgMbiY8RdzcMl1F0603xpIdaCo+f1VNAWiEF4qgB+Cl8rIrYas
vlkFGWyxnmVt/kBGtc5Q9BPlHXqygaks+OZfNjy6Wd4wD8AcAty2mK3AajRaNF1i
8VLCurIKlhCKdHVuU9z3lhqUgoYc173RheKRPks5E3JjlbdLSYWO0t/u62u32c7m
mkulpg==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIFoDCCA4igAwIBAgIUc8kGDBA5ihcMvJN17wRr86svbmUwDQYJKoZIhvcNAQEL
BQAwUTEZMBcGA1UEAwwQUXJhdG9yIFN5c2xvZyBDQTEUMBIGA1UECgwLUXJhdG9y
IExhYnMxHjAcBgkqhkiG9w0BCQEWD21haWxAcXJhdG9yLm5ldDAeFw0yMTA3MTIx
NTU4NDVaFw0yNjA3MTExNTU4NDVaME8xFDASBgNVBAoMC1FyYXRvciBMYWJzMRcw
FQYDVQQDDA4xNzguMjQ4LjIzOS4zMDEeMBwGCSqGSIb3DQEJARYPbWFpbEBxcmF0
b3IubmV0MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAusYLrODkJPkf
OhZzaLupR+yO1L5SxDka8tW89Mf8mYkpmLPVd42B/8Zw4aqR+YYmsvob8sJYlhv6
zPl1dRocPZ3qXkbvVRj+IrWWzKRvVIiN7RS/Ducw+PcDxWA+3Gq7YFO2z8nxctn2
YqfIUCsitjQAFxx/UNpCvk3w1gQUSsDh2rPvZZNy1DlmpKyOArkA8r3qaLqY55vk
qq37cHDsf+ycZxQ4cj8Yxj+yltX7XIx7nOcE/s2esb/fzeqB0fVxugZe3Cqumkq+
oI3m0NJsT/F35hu4eFlqK/yRvmwsFqgFBozZ2FuyxStWocYdKyYYIe3OX1NQSS2y
1f1FRPwae6MAydnotHmBRCWdrFK38y7AdmztcFN68qF9iKG5WhOk3sAg39Korlt/
86Ki3Eeggml4IkKPxi7bOW+fCVIJCN7y2eMMUlZVDabJk1Bq0nwZ1f+UEmYXBJ7L
Ys5rr71hpTcjYe2QFjZH6FtIRbMwlW5tLY31OR1iy9ybDZmirbQVfEXSdokDBZjm
W5UhrnWipO0XFek74WffnbGaOmbDUL4iFvfzR1qOO/YTB5LK3RzXZesl0kSk3InK
eXhcSTjeGLisxiSsGRlZqcJhA4tHywr0poIZvMeZHoejsTgvvAxhaCSX0NbWj88u
Qbrkl4FqzLJdtaAt3KhCtPfwaZi9QDMCAwEAAaNyMHAwHQYDVR0OBBYEFPWE0qob
GzPsWrrg22lwhjsAtqiHMB8GA1UdIwQYMBaAFGyR/xVNsHdETvLwhPDkBYlAEBAo
MAkGA1UdEwQCMAAwDgYDVR0PAQH/BAQDAgXgMBMGA1UdJQQMMAoGCCsGAQUFBwMB
MA0GCSqGSIb3DQEBCwUAA4ICAQCXUK7ZZZlJAgoyXKwU5z7lkytelxl26+GDckSY
TWXPybdT2KvIbM6jddpo/I3Hg8TT/gciqqApH1Qu0R/pGBRrN9e6Vo2Xryav7W5P
cXDMvm429nc8WofIwse9y1LhxZqeWG5cMq7hMQ0YQ3wU4NBNEPPF7Xd5pd29DVAQ
qwIBZ56QbG+J1KWd442MoQDU8bBQ2jzpmHIDP4BQ9EibQWvXigfmwdJ37qWHGoAC
XSsI/7UyVlxrwDOSe+KeytkcWWvMK3rjjustsOKipDplwBlP6uUkZiej2N6GrErC
HlOOWVgakoGxIJVnho3XliV+HEi22MJnTqqWqJ9uhvAqlUFcvtoqDzTV1JMuj2k+
s5ZBM9850PLr8vAbLRhMZ+MRBzHJefVxrXad5AVdUumiAnkB0sk89I9taL4RKUWP
PEJwqhRMWH0YGtXGl0NW2NtH3TlPWwVSRrrZwfJ09wZkax9M0wWfGsSNHgqwSz5G
h4XZVqbLsx8bxA5VJ3xIOdxZNufQwf5AERD6gQn6nii3KSe62VzFz136kjaW+C1i
dF8R93rZuTbIrZ1FCbTbvkGDgyNZvh2vIDExBt9SqGb1LLocDNdoe3EZEdzzloh6
AhVSmWbs5aYOaWOXHCK9dyfN3XuLp3gc6xAv22Uc8qd0UylFMsYfb1O/aAmDrZFH
LxXXJg==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIFkzCCA3ugAwIBAgIUcxyD6H7FyVjwmFXONIP8wFkEkJcwDQYJKoZIhvcNAQEL
BQAwUTEZMBcGA1UEAwwQUXJhdG9yIFN5c2xvZyBDQTEUMBIGA1UECgwLUXJhdG9y
IExhYnMxHjAcBgkqhkiG9w0BCQEWD21haWxAcXJhdG9yLm5ldDAeFw0yMTA3MDgx
NzIzMjFaFw0zMTA3MDYxNzIzMjFaMFExGTAXBgNVBAMMEFFyYXRvciBTeXNsb2cg
Q0ExFDASBgNVBAoMC1FyYXRvciBMYWJzMR4wHAYJKoZIhvcNAQkBFg9tYWlsQHFy
YXRvci5uZXQwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCZCZwSsOxW
weDPf4L5DUQRWUw3YeBucEGVVa7l3QKn0SbZPn4vZeu8Zvp93VcQSAOLiqI53oO0
I87Xk1pQKviy7tFWnHD9+XO4dyrsPJLSTKMQDR2RpncvbSfUvHmOOacLyL7m91oO
EL3g19Z1B2QedNM7js+QHzRGRolNUAJkAgDxpvzovTY+Yvnhg6JNJf78hSg7lIgs
SVl7BUnx+SOc7CYY+I9fR2Q/1gBX/qp+hB9r09VSQ95X1Qc1SlbaVo3T2ECiDhTJ
t4jNNXRtbB6IKeWPlNbXrOfQlx9NWKI2f0dTDcRaZuLxhSG/zrJOIuMxccNp+EXN
CpMMqSDknh2fvJ7QCrOpdSjT06OsELj59flGAiYmhcx4VLZ7FIHl/w/EOkFL3ktB
W5JnNd6y4NTNBUkP1PQlPnu7/bsQGVPBCowuCqjf1ETyJquh26JtSMUoDMGffFcA
4zHkRs8rRqWLKarzY8MHAHr0kOb+LTFJ5EhrmvsL+YCNV9wNDFBXP3sh8ld6TQUK
FSMeR12Bake5iphCt6rmxlfbXy177zrKHlGNGaA3naBv1zgqmkkQTTh8BcliEwBG
4yG6zDILNYs8/xIcg79B4cPiJ/D4XJPyOH+qIWFwhxjjzALb/gg6x8/k5ZNR/N+O
5kX6DpJIZeEN0qJ0BZRnaYFr9Sxlmwy+wQIDAQABo2MwYTAdBgNVHQ4EFgQUbJH/
FU2wd0RO8vCE8OQFiUAQECgwHwYDVR0jBBgwFoAUbJH/FU2wd0RO8vCE8OQFiUAQ
ECgwDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8EBAMCAYYwDQYJKoZIhvcNAQEL
BQADggIBABpdGyoHoiR9w4x0kAh/iZisb0bEHbMQjeJmv3Sh6+Be3ZVM7EgpNMB4
5PpiXfOLVjvc8iLa5d/neTi86Lh7ADhStJ14yOZAfyjZnrdtJaYixZQBaw9QWp1v
w3iYaygHe2x+oDgPjWcsaSBWAG/VkpNwNWnW1cx5PzdZjheHU/4vEW6SutAVts0V
np7Gdk1DAoNnVVpgZI9qO9d0+nJ5Hve8w5AWSFHWPqutC3vqsfYOhAmjeCxeAuH6
ArtWieH8uG1DyG6EId1iPyffAmR6na+ef7x+1+/f8BgwlBfvpa+Fl2myYgActayv
jR4gNauWWu56puGuNQoAPlLnqYcs0oDjG7yAlshE/Eupu90qOnY/ihedk865y8CM
nHTdvMK9Hr2FYZ8W1Fx89u558te5de90F3JHVEEA9KuB68fgqmEPUxbCHe8OUwbD
KcKbQoC/pPmAXJJw1x3pWCfgum+7meWwZJKa6BexN5Tcy/bYL+rtsK+Gal8jaKuD
hXy8lobCZ05q735YjAWN1UuHd3iEqDb6RHbsuMFBkS0uBvcnIgj8r/jGmUz2NdtN
PZ9ucR22fNR2ntL+UjXeppQp1Owg11wdjvb+8GfYyu8ir3rY9E1dPmmEoZaU6rpJ
57mrSgk8Rgxrq1aiTCT+1FQoCuHffn+VQA6deRKkwXYnx3opeAzo
-----END CERTIFICATE-----